Search
Don’t upgrade Lemmy past 0.19.3. Serious/significant regressions intoduced.
cross-posted from: https://sopuli.xyz/post/14184367
> Lemmy version 0.19.4 introduces 3 relatively intolerable bugs, and 0.19.5 only fixes one of them. > > * cannot post, risk of data loss > * cannot cross-post, but no data loss. > * can only visit the default timeline view >
Post edits appear accepted but get discarded
This may be an instance-specific problem because I’ve had no problem editing posts on other instances. When I try to exit the title and body of this post, I click save (or whatever) and without error it behaves as if my change was accepted.
Most instances take a minute or two to re-render the screen to show my updates. If the wait is long, I sometimes do a hard refresh to make sure the change got accepted (and if I don’t do that and I do another update, the old content populates the form and causes the recent edit to be lost).
Anyway, with infosec.pub my edits on the above-mentioned post just take no effect, confirmed by a hard-refresh showing no change.
Information Security Community Interest
ALL,
I have noticed a bunch of slightly overlapping communities, or some that just don't seem super active.
There are a couple of security related news communities already.
Is there actually interest in INFOSEC projects, blogs, frameworks, TTPs, etc?
Perhaps people who are interested would weigh in, and we could pick a community to work in? I know people don't always like the idea of consolidation, but I'm more interested in gauging people's continued interest.
- Do people here actively work on info sec projects that would post walk throughs, configs?
- Do people work within security frameworks and have sharable configurations?
@[email protected] @[email protected] @[email protected] @[email protected] @[email protected] @[email protected] @[email protected] @[email protected]
Hey @jerry, do you have any backup? Is there any way we can help you?
As the title says, @[email protected] do you have any backup and how can we support you as the admin of our instance?
Burnout on spare-time projects can be very real, especially when they suddenly grow or become more difficult to manage. We all appreciate what you are doing here. So even if there's nothing we can do directly, I'd just like to say thank you.
BusKill (USB Dead Man Switch) v0.7.0 released 💾
We're happy to announce the release of BusKill App v0.7.0. This release includes bug fixes and introduces a new GUI "soft-shutdown" trigger.

We're happy to announce the release of BusKill v0.7.0!
[!BusKill Release Announcement v0.7.0](https://www.buskill.in/buskill-v0-7-0-released/)
Most importantly, this release allows you to arm the BusKill GUI app such that it shuts-down your computer when the BusKill cable's connection to the computer is severed.
What is BusKill?
BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer.
| [!What is BusKill? (Explainer Video)](https://www.buskill.in/#demo) | |:--:| | Watch the BusKill Explainer Video for more info youtube.com/v/qPwyoD_cQR4 |
If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device.
Upgrading
You can upgrade your BusKill app to the latest version either by
- Clicking "Update" in the app or
- Downloading it from GitHub
Changes
This update includes many bug fixes and new features, including:
- Adds support for 'soft-shutdown' trigger to GUI
- Adds a new
buskill.iniconfig file - Adds a new "Settings" screen in GUI
- Merges kivy & buskill config files into one standardized location
- Fixes in-app updates on MacOS
- Fixes lockscreen trigger on Linux Mint Cinnamon
- Fixes background blue/red disarm/arm color to propagate to all screens
- Fixes
--run-triggerto be executed inside usb_handler child process and communicate to root_child through the parent process
You can find our changelog here:
Documentation Improvements
We've also made many improvements to our documentation
- Updated the Software User Guide to include how to arm the BusKill app with the
soft-shutdowntrigger in the GUI - Added a manpage
- Better documentation on how to build your own USB-C BusKill Cable
- Better documentation on how to test the buskill app
- Fixes in Release Workflow
- Added some additional related projects to our documentation
Soft-Shutdown Trigger
This release now allows you to choose between either \[a\] locking your screen or \[b\] shutting down your computer when you arm the BusKill app from the GUI. By default, the BusKill app will trigger the lockscreen. To choose the 'soft-shutdown' trigger, open the navigation drawer, go to the Settings Screen, click Trigger, and change the selected trigger from lock-screen to soft-shutdown. For more information, see our Software GUI User Guide.
BusKill Now in Debian!
We're also happy to announce that, with the release of Debian 12, it's now possible to install BusKill in Debian with Apt!
sudo apt-get install buskill
Testers Needed!
We do our best to test the BusKill app on Linux, Windows, and MacOS. But unfortunately it's possible that our app doesn't fully function on all versions, distributions, and flavours of these three platforms.
We could really use your help testing the BusKill app, especially if you have access to a system that's not (yet) listed in our Supported Platforms.
And in this release, we specifically would like you to help us test the new soft shutdown feature. Please let us know if it does or does not work for you.
Please contact us if you'd like to help test the BusKill app :)
PSA: Lemmy.world was compromised!
Discussion from here: https://lemmy.ml/post/1895271
Relevance: Infosec.pub may wish to consider defederation temporarily.
Temporary fix in place, but instances remain vulnerable. Post: https://lemmy.world/post/1290412
- UPDATE 2:58 UTC the injected code was removed from the main page, but cleanup efforts are still underway.
- UPDATE 3:11 UTC situation appears to be under control, but browse with caution.
- UPDATE 3:35 UTC main page exploited again! Website is unsafe.
- UPDATE 4:01 UTC reports coming in that other instances are getting owned. One report of comments trying to inject JavaScript into the page.
- UPDATE 4:13 UTC XSS vulnerability in page sidebar is reported relationship to the event is unknown.
- UPDATE 7:17 UTC Root cause was identified a while ago.
What 'app' are you using to view infosec.pub
Since Lemmy is so new, and the default interface is not always that ... great (yet), ~dispite @[email protected] best efforts~
what app do you use to view posts on here?
I was using wefwef.app and am considering hosting my own. what do you all use?
current Tally:
Malicious actions originating from infosec.pub?
Found the error Not allowed to load local resource: file:///etc/passwd while looking at infosec.pub’s communities page. There’s a community called “ignore me” that adds a few image tags trying to steal your passwd file. You have to be extremely poorly configured for this to work, but the red flags y...
Hi, I saw this Beehaw post while browsing All. Anything we need to be concerned about?
EDIT: False alarm, see himazawa's response.
(https://infosec.pub/c/infosecpub) testing posting from (https://infosec.exchange/tags/mastodon)
@infosecpub testing posting from #mastodon
Testing, testing, 1, 2, 3...
Growing infosec.pub
@[email protected] I took the liberty to promote this instance a bit here, the post is this one.
I'd like to help growing a community, is there anything we could do?
Thank you Jerry!


Just wanted to say thank you for putting this Instance up. It seems lightning fast and I had no trouble logging in, unlike almost all the other Lemmy instances I tried during this mass Reddit exodus.
Really appreciate you @[email protected]!
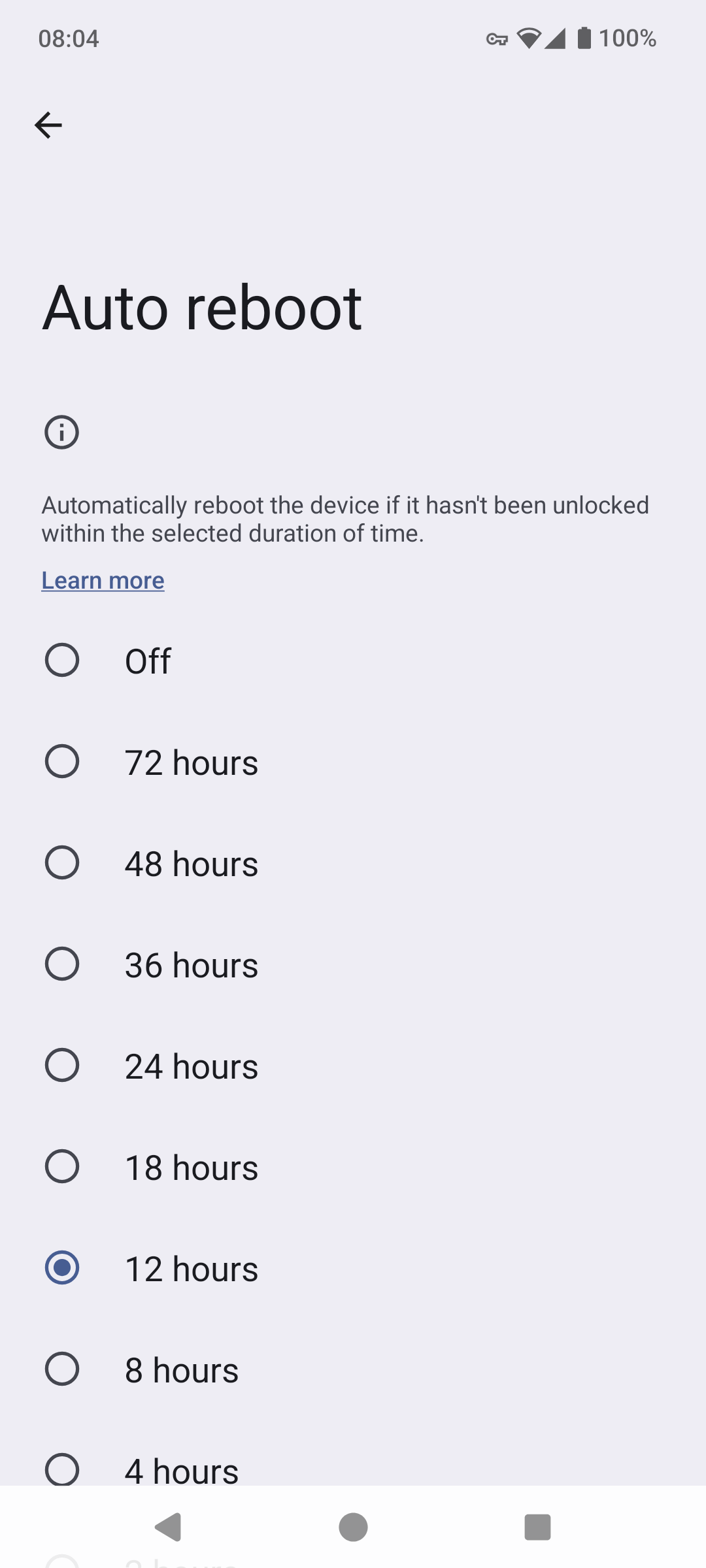
The article mentions they suspect being disconnected from the network causes the reboot. That's a great idea. That should be implemented as well on gos.
@return2ozma This ships don’t work and are being decommissioned. Most of the time they are in a port being repaired. You can’t blame them wanting a connection to the world.
https://www.propublica.org/article/how-navy-spent-billions-littoral-combat-ship
You might prefer smaller instances; … This part of it is clearly not a bug, however you put it. It is a difference of preference.
My personal preference happens to align with fedi principles. Don’t let that consistency fool you. I’m not advocating for what’s best for me. I am saying the list should be ordered in a way that’s healthy for the fedi based on the federation’s purpose and mission.
Showing the biggest communities on top may be your personal preference, but that is not healthy for the federation.
I myself am on an instance that’s almost identical in size to yours.
FYI, aussie.zone is centralized on a US tech giant (Cloudflare) and thus contrary to fedi principles. Though it’s not the worst manifestation of Cloudflare because they have whitelisted Tor. But there are still many other demographics of people likely being excluded from aussie.zone.
I do not see the value in smaller communities being prioritised when they each cover the same topic. If there’s [email protected] with 10,000 subscribers and [email protected] with me and my twelve mates, lemmy.world is the one the app should show people first. It wouldn’t matter to me whether that 10,000 is on lemmy.world or midwest.social, it makes sense to show users the place they’re likely to have the most interaction.
That is not healthy for the federation. That imbalance is a problem that Lemmy has failed to control. The disproportionately large communities need no promotion. Too many people know about them already. They should either not be listed at all or be pushed lower on the list. It’s an extra slap in the face and injustice that these are exclusive Cloudflare instances that are getting prioritized. These are instances without self-control on their growth and power.
It’s not instance-related at all.
It is instance related. If you search for Android on other instances you will get different lists. Users on infosec.pub have subscribed to every Android community in existence which makes the manifestation of the problem unique to infosec.pub. The [email protected] community is also federated to infosec.pub by way of my subscription. It is true to fedi principles of inclusion and decentralization, unlike those that get listed on the top. So it’s an unhealthy sequence.
It could even be one user account that caused this. The activism.openworlds.info Mastodon instance was getting hammered with traffic. After investigation, they discovered that one user was following a shit ton of other accounts. All those follows were responsible for the admins struggling to cope with all the traffic. That instance eventually went under because it could not cope with the bandwidth demands.
This belongs in discussion around lemmy-ui, the various Lemmy apps & alternative front-ends, or in Lemmy itself with what gets returned by its search API.
The software part of the problem is specifically in the stock Lemmy web client. The bug tracker for the Lemmy web client is jailed in MS Github’s walled garden, hence why it was originally posted in [email protected]. There may be a configuration element to this, which is why it’s posted in this infosec.pub community. If there is an inactive account with all these android subscriptions, that can be remedied on the instance.
order should be descending order of size.
If bigger is better, why are you here instead of Facebook and Twitter? Fedi principles and philosophy have completely escaped you. In the fedi, we consider power imbalances, privacy abuses, and exclusivity resulting from centralization to not only worsen UX but to be an injustice. Encouraging disproportionate growth in the fedi is to advocate the destruction of what brings us here.
Unfortunately they seem not to be active on Lemmy anymore. The other admin, @[email protected] is though, so maybe they have some idea?
You might have to @[email protected] if there isn't notes on why listed. Sometimes instances get compromised and flood bad stuff. Maybe the instance can be enabled if there's no other reason to keep it disabled.
@[email protected] Would you share any of the following, I'm just curious:
- what's rough user count
- what's average instance CPU, memory, bandwidth use
- database and file storage
- cost
- time commitment
- Colo, business, residential
[edited this report to update with correct info] My workflow is I click on create post, post the URL of the media, upload a small image of the logo, add the body text with links to the conference information and meda.
The issue is that when I add the image, the URL of the image gets put into the URL field of the create post page.
Previously the URL in the create post page could be directly to the YouTube video. For example https://infosec.pub/post/3334303 worked fine.
even when: @jerry and @shellSharks are working on the servers. and I have nothing but praise for them.
I also think there should be some (small) group of people able to help & assist with the task of maintenance and support of the backend.
(and i don't mean getting root access to anyone's hardware, especially not without vetting)
and I would also think it would be a good idea to have some (open) scenario / manual / strategies for different standard actions, preferably with a script to also fix the issue.
(just some ideas running through my brain)
First of all thanks for the very detailed response. I have a few questions.
-
Like you said, why not use public key cryptography? Why is it not well supported for web-apps?
-
Why not use something like Diffie-Hellman algorithm to share the password? Signal protocol uses ECDHE so I am assuming that it's safe against mitm which the base Diffie-Hellman is vulnerable to (I might be wrong. I couldn't find if it waa vulnerable or not).
The 2FA process itself - both initial setup and use with an OTP provider - has worked consistently for me so far. The instruction in the interface is misleading and I'm not the only one who locked himself out as a result. The Mastodon devs merged my pull request to clarify the instruction (including my mistake of saying "oauth" instead of "otpauth") astonishingly quickly.
If I may be constructively critical, we should expect to provide provide at least some minimal evidence to justify claims such as one that something doesn't work, even if only as a link to discussion or evidence. This expectation increases when it's accompanied by advice or instruction, especially when such advice is counter to advice which is generally accepted as "good".
As @[email protected] mentions, a more serious problem of password reset via email disabling 2FA offers a workaround for now in at least some cases.
Everything was good for a while, but the 500s are back here on Fedia, particularly on index pages :(
@lefractal @infosecpub if you never got the confirmation email you won't be able to login I would message @jerry about confirming your account. He is going to need your username on @infosecpub to fix it.
@Spellbind0127 @infosecpub
Hey, I got the same issue when I try to login using a brand new account. Using username or email yields the same "spinner of death" :(
I also never got a confirmation email, but I don't remember the UI telling me there was any error with my account.
I also tried using another browser without crap-blocker, and even without any vpn connection.
Is this temporary overload or is there something I can do to fix this ?
@shellsharks @infosecpub testing a reply
I haven't done any testing with pixelfed yet. Creating an account is on my list of things to do though. Testing would likely come sometime after that.

