Search
Private videoconferencing ?
Hi,
I'm looking for a E2EE and decentralized (or self hosted) videoconferencing that would have the following feature
- video or voice-only call
- share screen
- files transfer (optional)
- text chat
( all of it E2EE )
I'm considering Jitsi meet, that seem the meet those requirements
Do you know better alternatives or do you have remarks about Jitsi ?
Thanks.
Using TrackerControl
Mornin' Been wondering if I should install GOS on my Pixel8 or keep my present setup with TC. I'm not conversant with the mechanics behind TC but it feels right to me. I don't use Google Apps and have been on F-Droid more often then Google Play. I do have a few apps which require net access hence using TC.
What say you..?
What do you think of AdNauseam and their 'poisoning-the-well' approach?
Inspired by the discussion in 'they already have your data' I was reminded that AdNauseam exists. I rarely see it mentioned in privacy circles but the idea seems attractive to me, I've used it before and since it's based on uBlock Origin it was just as effective in adblocking and the "poisoning" itself unobtrusive. How do you guys feel about it? Are there reasons it should be avoided?
It seems like YouTube have changed their link tracking to include more information
Up until like a year or two ago, YouTube links always used to be pretty clean. The format was youtube .com/watch?v=[video_ID]. A year or two ago, they started adding a tracking suffix on, so it would be youtube .com/watch?v=[video_ID] &si=[tracking_ID].
Over the last day or so, I've noticed links with a different format, youtube .com/watch?v=[video_ID]&pp=[tracking_ID] - only the pp= string is much longer than the si= string. This can only be because they're including more information in it. What that information is is anyone's guess.
This is basically a PSA to watch YouTube links more carefully, as people are by and large complacent with them (moreso than other links) and never even realised the si= change, let alone this new pp= change.
It could also be that the change to pp= is meant to circumvent communities, like this one, which automatically filter out the si= suffix. They may have decided to address that, then took the opportunity to make their tracking more severe.
Installed #GrapheneOS several days ago on my Pixel 8. It works great without any Google services!
Installed #GrapheneOS several days ago on my Pixel 8. It works great without any Google services! https://grapheneos.org/
I answered: Is there an expectation of privacy in public?
@[email protected] wanted to know, should you expect privacy in public places?
Before I answer that, I would like to give my genuine thanks to everyone who responded in my previous post where I asked you for some controversial privacy topics. You did not disappoint, and I'm glad I will be able to cover them!
This question is a bit complex, depending on how you ask it. The answer also largely depends on what you believe. If you believe that privacy is a fundamental right, then privacy should be expected no matter where you go. If the question is "Can you expect privacy..." versus "Should there be privacy...", the answer changes dramatically.
Is there currently privacy in public spaces?
In many places, there is little to no privacy when you walk out the door. With Ring doorbells latching on to every home like a parasite, or security cameras clinging to the ceiling of every store you walk inside, surveillance is everywhere. This section won't cover whether or not surveillance is moral/ethical/justified, but either way surveillance infringes on privacy. Even with no surveillance cameras, Sarah-from-down-the-street is always on a video call with her bestie.
Saying "privacy in public" is a bit of an oxymoron, since no matter what you will always give up a little privacy the moment you walk out the door. Things you do privately in the bathroom are simply not allowed in public places.
Should there be more privacy in public spaces?
Now may be a good time to clear up a common misconception. What is privacy? Privacy does not mean obscuring every detail of your life. Privacy is the ability or choice to share or hide information about yourself. That is why surveillance cameras infringe on privacy: You have no control over what they record, who has access to those recordings, and what those recordings will be used for.
That sort of answers the question, too. If you believe privacy is a fundamental right, then there should be an expectation of privacy in public spaces, and so a reform needs to happen.
What are the real effects of privacy in public spaces?
People act differently when they know they are being surveilled. See the Panopticon for an experiment about that. It has negative effects, whether people realize or not.
@[email protected] told a story that I particularly love:
"Just last week, my partner and I were on a long hike. No one was around us so to loosen our muscles we started dancing like goofballs on the trail only to look up and find a drone hovering in the shadows recording us. I was embarrassed, but my partner is a very private person and was really upset. [...]"
When they expected to be in a secluded, private space, they freely expressed themselves. The moment they realized that someone had been watching, they became embarrassed or upset, like a switch had flipped. That is the real affect surveillance has on us. We express ourselves less freely, we conform to rules without question out of fear. Surveillance becomes a form of oppression on a wide scale.
I even have my own anecdote. I once took a trip to a small town. When I got there, I subconsciously looked around for security cameras. I do that to gauge how much privacy I currently have. I then noticed that I couldn't see any obvious security cameras. I stopped and looked around harder. The town had not a single security camera in sight. I have almost no way to describe the sense of calm and relaxation that washed over me. It felt like someone giving you a massage after being stressed all week, or finally being honest with everyone about a secret you've been keeping. It was such a nice feeling to walk around a town privately.
Why do we have surveillance?
The main justification for these surveillance measures is to prevent crime. It makes sense intuitively, if you have an eye on every corner you can catch any criminal easily. However, it ignores one massive flaw: criminals will always find a way to do things privately. If you make privacy illegal, it doesn't change anything, because criminals won't follow the law anyways.
I have my own quote about this, that I love very much: “Unjust laws only burden the just, as the lawless will not heed them.” Removing privacy only hurts the people who will follow and abide by the rules. You're removing the privacy of the good people, while the criminals will program "illegal" software to achieve privacy. Giving privacy to everyone means that, yes, it makes criminals' jobs easier, but it means we can shift to actually solving the problems that cause the crimes in the first place. "The best way to conquer bad ideas is with better ideas, not by suppressing ideas." - Naomi Brockwell
"The optimal crime rate is not zero. We can't burn down the entire world just to stop somebody from stealing a pack of gum. The cost is too high. There is a percentage of crime that is going to exist. It's not ideal, but it is optimal." - Nick We need privacy for a free society. Surveillance is not the answer for fighting crime. There are ways to combat crime without infringing on privacy.
Is blurring your house on the map unreasonable?
This question is another one brought up by @[email protected]. Blurring your house is a way to achieve some privacy, and in that scope, it is good to do. However, as @[email protected] points out, it could cause someone to do the opposite and start looking closer into why your house is blurred. That's called the Streisand effect.
Site note: I find it hilarious why the Streisand effect is named how it is. The story goes that Barbra Streisand tried to hide her place of residence by suppressing a photograph that had made it to the public. That, of course, had the opposite effect, drawing more attention to the photograph and her residence. Then, even more attention was drawn, because the Streisand effect got named after her and the very same image is now plastered on Wikipedia.
Unfortunately, blurring your house on the map doesn't provide much privacy, since the organization who photographed it still has a clear picture of it. It doesn't stop the surveillance. It's not unreasonable to blur it, though. You should still want privacy against the Streisand effect. The best solution would be a quiet legal take down of the images altogether.
I have another story to go along with this. I got a job, and it was later revealed in conversation to me and my coworkers that our boss likes to look up everybody's address on Google Street View. Everyone was uncomfortable with that, but our boss saw no issue with it. This is a legitimate case where blurring your house is a good idea. Sure, people may try to ask you why it's blurred, or try to look up pictures on other sites like housing retail, but it still prevents (frankly, creepy) bosses from snooping at your home.
Conclusion
Privacy is a fundamental part of our lives, and surveillance infringes on that. We should all do our part to gain what privacy we can, because every bit of privacy you gain now is freedom you will have in the future. This was a lot of fun to write, and I thank @[email protected] and all of you for your suggestions. I will continue to tackle each of the topics asked in the previous post one by one.
Thank you for reading!
\- The 8232 Project
Take a break from Twitter


cross-posted from: https://monero.town/post/5041387
> Take a break from Twitter > > - If you use the Tor Browser or the Mullvad Browser you will see the popup of NoScript - because your identity at X can be open to other websites in your web browser. Keep your privacy in mind. > > - You may leave traces without realizing it. The way you write, what you read about and how much, when you are active, etc. Remember, if you are a Monero XMR user, you may not want this at all! > > - Mental hygiene; it feels good not to be at the mercy of the posts there for a while. Try it out! > > - It usually takes up a lot of your time without you doing anything productive. > > - Elon Musk himself is a major disinformation disseminator on his own platform. But many of the posts there are also questionable. > > - X Using Your Tweets to Train Its AI. And even if you have deactivated the artificial intelligence option, the users you interact with probably haven't deactivated it. Because it was introduced without notifying the users.
What are some controversial privacy topics?
If you don't know me, I make frequent write ups about privacy and security. I've covered some controversial topics in the past, such as whether or not Chromium is more secure than Firefox. Well, I will try my hand again at taking a look at some controversial topics.
I need ideas, though. So far, I would like to cover the controversy about Brave, controversy around Monero and other cryptocurrencies, and controversy around AI. These will be far easier to research and manage than Chromium vs. Firefox, for example. I'd like to know which ideas you have!
Which controversial privacy topics do you know of that you would like to see covered?
PLEASE DO NOT ARGUE ABOUT THEM IN THE COMMENTS!
Please save any debate for if/when I make a write up about the topic. Keep the comments clean, and simply upvote ideas you would like to see covered. I won't be able to cover everything, so it helps bring attention!
Above all else, be kind, even if you don't agree with an idea or topic :)
A hilarious attempt at phishing.


So I was checking my Proton Mail inbox, as I usually do, when I came across a hilarious email in my spam folder.
> Your Mailbox storage is 99% full > > You are currently using 4852.3 MB of 5000.00 MB available > > Don't risk losing new incoming messages, Follow below to increase your email account storage. > > Increase Your Email Storage
I was very careful not to click on any links in the email.
I was not fooled even for a second. It was impossible for me to have run out of storage. You know why? Because I paid for a Proton Unlimited subscription a few months ago, and I have more than enough storage!
The fact that I got this email means someone got access to my email address, which makes it hard to narrow it down because I used to sign up for a LOT of services. I've started using Addy to create new aliases, but I really wish I had done that sooner, so I could see who sold me out.
Here's a lesson: always use an email alias, so that when/if this happens, you'll know who leaked your email address!
If your car connects to the internet, what personal data could it be sharing – and even selling? A new report on Australia’s 15 most popular car brands reveals these privacy concerns.

> New research reveals serious privacy flaws in the data practices of new internet connected cars in Australia. It’s yet another reason why we need urgent reform of privacy laws. > > Modern cars are increasingly equipped with internet-enabled features. Your “connected car” might automatically detect an accident and call emergency services, or send a notification if a child is left in the back seat. > > But connected cars are also sophisticated surveillance devices. The data they collect can create a highly revealing picture of each driver. If this data is misused, it can result in privacy and security threats. > > A report published today analysed the privacy terms from 15 of the most popular new car brands that sell connected cars in Australia.
Where can I submit a large list of spam emails?
I accidentally had my forgejo instance open for registration. When I noticed it, there were tons of fake accounts open, with empty repos opened for each account. All of them had emails associated with them. They might've just been trying to annoy me, or maybe there was some plan to be executed later, since they'd have access to basically free storage, without any tracking.
In any case, I have cleaned all of it, and now have a list of 19311 usernames and emails. Maybe I can submit these somewhere for a spam filter? Idk, just curious if there's any point in keeping this list.
A New Force Is Rising
>We Need New Troops > >You might remember a few months ago I interviewed Phil Zimmermann, the creator of PGP, which became the most widely used email encryption software in the world. > >Phil and I spoke about the war against privacy in the early '90s. When Phil published his PGP code as free, open-source software, he wanted to help people protect their privacy. For this, the U.S. government investigated him for three years, claiming he was effectively trafficking munitions. > >Phil fought the government alongside a group of hackers and cryptographers known as the Cypherpunks, who stood firm in their belief that privacy is a fundamental human right. Phil laid out this argument in his essay titled Why I Wrote PGP, where he explained that without the ability to communicate privately, democracies slide into autocracies: > >> “The need for protecting our right to a private conversation has never been stronger. ... Ordinary citizens and grassroots political opposition groups need to protect themselves against these emerging autocracies as best as they can. If an autocracy inherits or builds a pervasive surveillance infrastructure, it becomes nearly impossible for political opposition to organize, as we can see in China. Secure communication is necessary for grassroots political opposition in those societies. … >> >>PGP is good for preserving democracy. If privacy is outlawed, only outlaws will have privacy.” > >These early battles, known as the First Crypto Wars (where "crypto" is short for cryptography), were won, and individuals were once again able to exercise their right to privacy in the digital age: > >>“It has been a long struggle, but we have finally won, at least on the export control front in the US. Now we must continue our efforts to deploy strong crypto, to blunt the effects increasing surveillance efforts on the Internet by various governments. And we still need to entrench our right to use it domestically over the objections of the FBI. PGP empowers people to take their privacy into their own hands. There has been a growing social need for it. That's why I wrote it.” > >This essay was written in 1999, and while the battle may have seemed won-and-done at the time, we have since found that it’s ongoing. > >Today, there is a massive assault on privacy, with hidden code in our apps tracking our activities, governments skirting checks and balances by purchasing vast amounts of data from brokers, and the normalization of surveillance creating a dangerous complacency around the loss of privacy. > >Phil Zimmermann has since realized: > >>“We are going to need fresh troops.” > >Learning From Battles of the Past > >We won’t win unless we inspire others to join our cause. During the First Crypto Wars, people were galvanized by rallying cries from pioneers like Phil Zimmermann and manifestos written by Cypherpunks like Tim May and Eric Hughes. > >I can’t possibly expect to reach their standards, but I have tried my hand at writing a manifesto. My hope is that it might contribute, in some small way, to encouraging people to join us. > >I have also soft-launched a new institute—a nonprofit dedicated to helping people maintain their freedom and dignity in the digital age. I haven’t officially announced it yet (you’ll hear more in the coming months), but our board of advisors is packed with inspiring Cypherpunks who fought these early privacy battles, including Phil Zimmermann himself. > >This manifesto may seem intense in a world where surveillance has become normalized. But we need to shift the Overton Window back to a place where individuals are empowered in their own lives. As Phil said in his essay, “There’s nothing wrong with asserting your privacy.” > >Here it is. Tell me what you think. > >The Priv/Acc Manifesto > >A new force is rising in the digital age, a force to reclaim what has been quietly stolen: privacy. > >We are the Privacy Accelerationists—driven by a simple conviction that privacy is not optional, but essential for personal freedom. Surveillance capitalism, government overreach, and the culture of data extraction corrode our ability to live freely, think independently, and interact with trust. > >The future of privacy is no longer something that can be delayed, debated, or dissected. It must be accelerated—now. The pace of intrusion is relentless; our response must be swifter still. The tools to protect privacy—encryption, decentralized networks, and privacy-enhancing technologies—already exist. But only decisive action can ensure these tools are put into the hands of billions. > >We are not radicals for desiring privacy, but because we understand that privacy is power—liberation in a world that seeks to control us. Privacy is rebellion. In a society where thoughts, desires, and behaviors are commodified for control, privacy becomes the means by which we reclaim our lives and identities. > >The systems of surveillance—corporate, governmental, and societal—are intertwined, feeding off each other in a symbiotic cycle. But as history shows, even the most entrenched systems are vulnerable to revolution. Cryptography is that revolution. Anonymous transactions, encrypted communications, decentralized data: these are not just theoretical tools but the foundations of a new era. > >Governments and corporations will attempt to stop us, justifying endless data collection with claims of “efficiency” or “security.” They will argue privacy is unnecessary in a world where transparency is a virtue. They will say, "If you have nothing to hide, you have nothing to fear." > >We reject these premises entirely. Privacy is not about hiding—it’s about choice. The choice of what to reveal, to whom, and when. Without privacy, there is no autonomy; without autonomy, there is no freedom. The acceleration of privacy technology is our only path forward. >We do not oppose technology—we champion it. Our fight is against the hijacking of technology to strip away privacy and autonomy. We assert our right to navigate the digital world without the oppressive gaze of surveillance. By embracing technology as a tool for empowerment, we can restore control over personal information to where it belongs—with the individual. This is our moral imperative, our stand for a future where freedom and technology coexist. > >The systems of control thrive on complacency and apathy. We are here to disrupt that cycle. We will accelerate the adoption of privacy-enhancing technologies—not as a slow reform, but as a revolution. Code is our weapon, and knowledge our shield. We build not for governments or corporations, but for people. > >Privacy is the cornerstone of an open society in the digital age. To build that society, we will work with cryptographers, developers, activists, and everyday users. We will create networks that resist censorship, tools that ensure anonymity, and communities that defend privacy at all costs. > >We will not wait for permission. We will not apologize for defending our right to exist unobserved. We are not products. We are not data points. We are free individuals. > >Join us, or stand aside. Privacy will not wait. > >Onward. > >Privacc.org
Hospitals in Kazakhstan will no longer provide medical services without Face ID
Денсаулық сақтау министрлігі медицина саласына жаңашылдықтар енгізуде

The original article is in Kazakh, so here is the translation via DeepL:
> Face ID will be introduced in Kazakhstan to combat [malicious] records in polyclinics, the Health Ministry said.
> A pilot project has already been launched on the basis of the republican polyclinic of primary health care in Astana [the capital of Kazakhstan].
> Under the project, patients will be identified using Face-ID and webcams, which will eliminate the possibility of falsifying data on services received, the Health Ministry said.
> "By the end of this year we will conduct a pilot project in Astana, and from January 1 we plan to scale it to the whole country. This will become an effective tool, which will eliminate imputations at the root."
"What Is Your Dream for Mozilla" - Mozilla is doing a survey, and it could be a good opportunity to share some of the feedback that usually gets commented here :)
cross-posted from: https://lemmy.ca/post/33165280
> I got a copy of the text from the email, and added it below, with personal information and link trackers removed. > > > Hello [receiver's name], > > > > I’ve long dreamed about working for Mozilla. I learned how to send encrypted e-mail using Mozilla Thunderbird, and I’ve been a Firefox user since almost as long as I can remember. In more recent years, I’ve been an avid follower of Mozilla’s advocacy work, and was lucky enough to partner with Mozilla on investigative journalism in my last job. > > > > In many ways, Mozilla was the dream – and now, as the leader of the Foundation, my job is to make my dreams for Mozilla come true. What that means, though, is making your dreams come true – for a trustworthy and open future of technology; for tech that is a tool for liberation, not limitation; and for tech that values people over profit. > > > > So I’m reaching out to technologists, activists, researchers, engineers, policy experts, and, most importantly, to you – the people who make up the Mozilla community – to ask a simple question. > > > > [receiver's name]. What is your dream for Mozilla? I invite you to take a moment to share your thoughts by completing this brief survey. > > > > Let’s start with this question: > > > > > > Question 1: What is most important to you right now about technology and the internet? > > > > > > - Protecting my privacy online > > > - Avoiding scams > > > - Choosing products, apps, technology, and services that I can trust > > > - Keeping children safe online > > > - Responsible use of AI > > > - Keeping the internet is open and free > > > - Knowing how to spot misinformation > > > - Other (please specify) > > > > Take the survey now → > > > > > > > > With your help, together we can imagine and create the Internet we want. Thank you for being a part of this. > > > > Always yours, > > > > Nabiha Syed > > Executive Director > > Mozilla Foundation
Which privacy-friendly search engines have advanced search functionalities similar to those Google provides?
Hi all,
I'm currently wanting to make a few wiki pages for a community I host here on PieFed. Not trying to advertise the community, but for context, it's a community about BY-NC-SA licensed music, and I'm wanting to create a guide as to how to find new music with that license on certain platforms.
My trouble is this. I want to provide those viewing posts with the ability to find music with ease utilizing search engines when that's the best option to do so. However, I also don't want to have that search engine be Google if that's at all possible.
The main features I'm needing are to only fetch results from certain websites, and to specifically include or exclude specific phrases. For example, if I wanted to find BY-NC-SA power metal music on BandCamp, and exclude songs from the band Blind Desire for some random reason, I'd have the following search:
In this case, Google only fetches results from bandcamp.com, only with the BY-NC-SA license, and only with the words "power metal" in the page, while also removing results from Blind Desire.
Are there any privacy-friendly options that have similar search features? Being made aware of an alternative like this will definitely help me kick what little reliance I have left on Google.
Thanks in advance.
The government plans to ban under-16s from social media platforms.
The government has taken a big step towards its goal of getting children and young teenagers off social media and revealed who would be covered by the ambitious ban.

The government is being pretty coy about the details, so most of the article is necessarily conjecture.
Selected excerpts from the article: >The definition of a social media service, as per the Online Safety Act > >An electronic service that satisfies the following conditions: > > 1. The sole or primary purpose of the service is to enable online social interaction between two or more end users; > 2. The service allows end users to link to, or interact with, some or all of the other end users; > 3. The service allows end users to post material on the service.
> Under the proposed changes, it will be the responsibility of social media companies to take reasonable steps to block people under 16.
> How will your age be verified? > >The government's legislation won't specify the technical method for proving a person's age. > >Several options are on the table, including providing ID and biometrics such as face scanning. > >The government's currently running an age assurance trial to assess all the methods, and it's scheduled to continue into 2025. > >Based on the results of that trial, eSafety commissioner Julie Inman Grant will make recommendations to platforms. > >It's possible that Australians will be asked to provide their IDs or biometric data directly to social media companies in order to use their platforms, but that's not guaranteed. > >Many of the big players, including Meta, have instead argued for the age verification onus to be placed on app stores, rather than individual platforms, as that would mean proving your age once — rather than every time you sign up to a platform. > >It's also possible that a third-party company that specialises in ID verification will act as a go-between between users and social media platforms. > >No matter which model is adopted, the prime minister has said privacy protections will be introduced to cover any data people end up providing.
The GrapheneOS team finally responded to my requests for a comment
I made this post, outlining my verdict about whether or not Chromium is more secure than Firefox. At the very end of the post, I noted "GrapheneOS did not respond to my requests for a comment."
Well, after weeks with no reply, they finally responded. I don't plan to do any more research about this topic, but this information is still incredibly valuable. Keep in mind the questions I asked the GrapheneOS team were created before I had done much research about the topic. Here are the questions and GrapheneOS's replies:
Does Firefox have isolation between tabs?
incomplete
Is Firefox's implementation of tab isolation as secure as Chromium's?
no, it's incomplete and their sandbox is significantly weaker across all platforms, but it varies based on platform
Firefox uses Fission to isolate embedded content from the main website. Is Fission used for tab isolation as well?
it's incomplete
Is Fission the main cause of concern about Firefox's security?
there are many ways in which it's less secure than Chromium, but the weak sandbox particularly that's entirely not implemented on Android is one of the main issues
Are there other reasons why Chromium is more secure than Firefox, besides Fission?
Chromium uses full garbage collection for a lot of the C++ objects, has much more hardened memory allocators for native allocation, has the V8 sandbox as another layer of security missing in Firefox before the OS sandbox, has much more fuzzing, auditing, etc. and much more modern exploit mitigations implemented too
Firefox is far behind in nearly every way and laid off a lot of their security people
Isolation of embedded content is important to prevent Spectre and Meltdown exploits, but is this actually something that an everyday user will be majorly affected by? It seems that, unless you are logging in through embedded content, there is far less risk associated with this from an everyday standpoint. Again, more security is obviously better, but is this as big of an issue as it's made out to be?
yes it impacts users because browser vulnerabilities are widely exploited in the wild and the OS sandbox is one of the main defenses against it, as is the V8 sandbox feature entirely missing in Firefox
Google heavily monitors for browser exploits and catches a lot of it happening in the wild
Mozilla / Firefox has little visibility into it
therefore, it's much more widely reported for Chrome but does not mean it isn't happening with Firefox regularly
Is Firefox less secure on Linux (besides Qubes, Tails, etc.) than other desktop operating systems?
Tails is not a hardened OS at all, that's a misconception about it, and it has nearly all the problems of desktop Linux
Firefox on desktop Linux has weaker sandboxing than elsewhere
on Android they haven't even implemented a content sandbox, although the OS provides an app sandbox around it as a whole but that's not the same thing
In which ways are Fission less secure than Chromium's Site Isolation?
it's not even completed yet, the issue is still open since not everything is isolated yet and there are known ways out
Does Brave provide the same privacy against fingerprinting as the Tor Browser?
Tor Browser's anti-fingerprinting is greatly overestimated and does not really work with JavaScript enabled, which it is for most users
Brave's is not strictly better or worse
neither anti-fingerprinting approach works well
Could you provide good resources for my article about the state of Firefox security on Android?
no, but it is awful, they don't even implement any content sandbox let alone site isolation, and have almost no exploit mitigations or anything implemented
Would it be easy for a developer to create a fork of Firefox for Android that uses isolatedProcess?
no, but it's easy for them to do it relative to doing it elsewhere
Would using isolatedProcess in Firefox fix isolation issues? If not, what would still need done?
no, but it would allow them to provide a content sandbox on Android and partial site isolation to the extent they implement it overall
Is there tab isolation for Firefox on Android? Is this as secure as Chromium's?
there's an incomplete implementation, and no, it's not nearly as secure aside from being incomplete
Can a Unified Push push server see/read notifications?
By "push server" I mean something like Ntfy.sh.
---
Cross-posts
- https://sh.itjust.works/post/27577324
Mobile hotspot with VPN: is GL.iNet the only game in town and is it trustworthy?
So I'm on the market for a 4G or 5G mobile hotspot with a build-in VPN client I can carry around in my backpack and connect my cellphone to. I've looked far and wide, and really the only manufacturer that seems to make what I want is GL.iNet.
The two battery-powered models they offer that interest me are the Mudi v2 and the Puli: they only do 4G and I wish they did 5G too, but I can live with that. Other than that, they really tick all the boxes for me.
From what I could read, the GL.iNet company also seems very open and very responsive. That's a plus too.
But I have one giant problem that prevents me from whipping out the credit card: GL.iNet is a Chinese company, and those products are sensitive applications. I know I can flash OpenWRT separately on those devices to ensure they're not doing stuff behind my back, but I don't really want to do that because I'd lose the GL.iNet plugins and custom UI. Not to mention, I have no free time for that. I'm looking for a ready-made solution if possible with this one.
Anybody knows if GL.iNet can be trusted?
Also, has anybody ordered from Europe using their EU store? They say they ship direct from Europe but they give no details.
And finally, what do you think of those two mobile VPN routers if you own one. Do they work well? I read somewhere that they can be buggy with certain VPN providers. Do they work in Europe? I assume they do since they sell EU plugs but maybe there are caveats.
The stock Fairphone runs the stock full-blown Google spyware stack. Privacy isn't Fairphone's selling point: it's repairability.
You can install CalyxOS very easily on it however. That's what I'm rocking on my Fairphone 4, and it's great. I have no issues with it.
I heard that he was a scammer or pseudo privacy expert from other comments. I wouldn't recommend that phone. If you care about the privacy or security of your device, use DivestOS with a supported Pixel/OnePlus, or GrapheneOS with a Pixel. Only buy the phone new if you are super paranoid of some zero-day vulnerability being used on you. I recommend swappa.com because they have quality control, returns, and good prices for used devices (you can even get mint quality devices).
Comparison of Android ROMs: https://eylenburg.github.io/android_comparison.htm
iodeOS has been behind on security updates often (still better security against unsophisticated attacks than Ubuntu but not a good ROM): https://divestos.org/pages/patch_history
Just tried that. Would appear it doesn't work if you can't check for an update. Can't figure out how to disable updates as I'm not that big into terminal use and can't find much online :/
I found this and actually like it better than Alpaca. Your mileage may vary, but they claim that it's 100% private, no internet necessary:
I'm kinda familiar with that rabbit hole :P . Though, I didn't quite consider your 3rd and 4th methods. So kudos to you for that!
While writing up a draft, I actually stumbled upon an (unfinished) article that goes over this subject in way more depth than I could.
Though, the author doesn't mention NovaCustom that intends to combine Boot Guard, Heads and QubesOS certification on their devices.
they have been going downhill for a while, proton has worked with the feds without resistance bbc article
Adding onto what's already on the thread, you can try look at the newer Element Call, which is an implementation of Matrix's native calls.
I've been using it a bit recently, since Jitsi seems to have stopped working reliably for me (to be frank, I've not put much effort into debugging it yet). It works well, but it's still early stage, lacking some features Jitsi has. If that one works for you, I recommend you stick to it.
The screenshot:
The UBL app isn't listed, hope it'll work 🙏

This is what kinda scares me. Pixels are/were the only phone I know with a green/gray screen problem. Can't find images online (probably can't find the right words to search for it)
Screenshot for you. Google is explicitly linked to for easy setup. F-Droid is not. "There is nothing" is simply disingenuous.
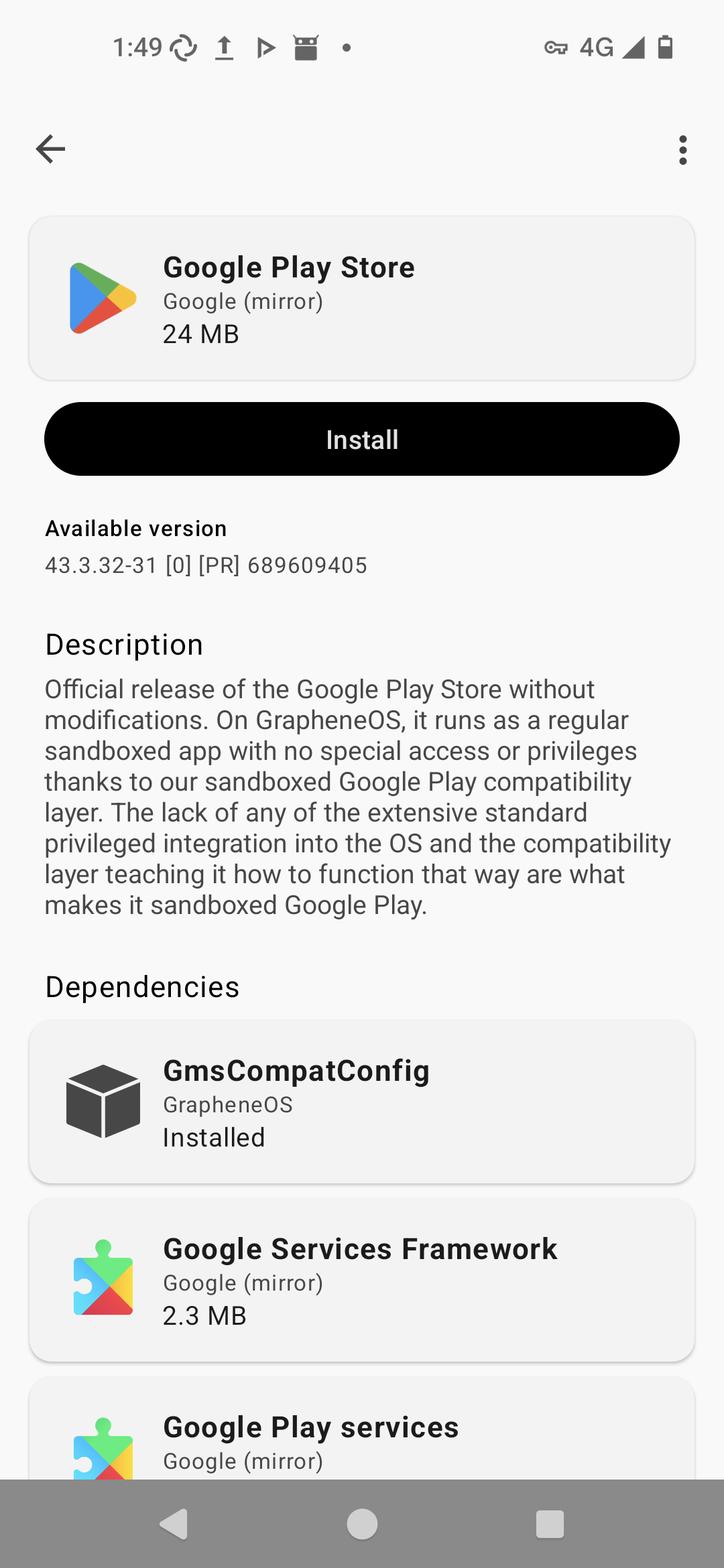
Do Google Pixel phones come installed with GrapheneOS? We're talking about custom setups with more privacy here.
I did have to follow the installation instructions, which included unlocking my bootloader, installing adb on my PC, and entering a few command lines.
There is the possibility to buy it preinstalled though, but from a third-party company.
You're probably going to end up on Jitsi meet, but I'm also going to drop a recommendation for bigbluebutton.
I recently noticed that it was integrated into the open source Learning-Management-System Canvas, which every school I have gone to so far uses.
Although bigbluebutton doesn't seem to explicitly support e2ee (but maybe this counts for something), if you are already using Canvas, BigBlueButton definitely worth looking at.
I really, really wish people at my school would use the integrated bigbluebutton instead of using zoom, especially given I've seen people occasionally have issues with authentication for zoom, but all of that stuff is handled with bigbluebutton because it's fully browser based and integrated into Canvas.
Using it since many years on many Pixels and loving it.
Main pros: zero bloat, efficient, highly secure and highly private (about as private and secure as it can get on any smartphone), and it's an Android without any of Android's typical weaknesses (privacy issues, bloat, etc.). You get to utilize the advantages of Google (its security) and completely avoid the disadvantages (its many privacy issues). You get to use all the advantages of an Android mobile OS while completely avoiding all of its disadvantages. It's like getting your cake and eating it too. You're much better off in terms of security and privacy than almost(?) all other smartphone users. According to leaked documents, Cellebrite for example can't crack GrapheneOS on Pixels at all. They can crack almost any other smartphone if they have physical access to it. Most smartphones are really easy for them to crack. iPhones may pose some trouble depending on model/OS. And Graphene on Pixel is the literal brick wall. And even on top of that it has tons of great security features, like auto-reboot after X hours of inactivity, charge-only-mode for USB-C when locked, distress/duress PIN entry to immediately wipe the phone, many things like that. On the privacy side it's looking great as well: Some folks have analyzed Graphene's network traffic and there's zero privacy issues from the OS or its built-in apps. And the few connections it does make (for updates and so on) are all documented and work exactly like they documented them, and they only transmit the exact least amount of necessary data without anything beyond that (guess what - that's super rare). And on top of that there's even more great privacy features, some of which are invisible but well thought-out, for example any SUPL request goes through a Graphene proxy server first (configurable) which strips all personally-identifiable data from the request and then redirects it to your provider's SUPL server (which is most likely Google's SUPL server in the end). I'm seriously impressed by the quality of the GrapheneOS project. Maybe you don't realize how good and rare such things are nowadays. Also the documentation is very good and actually answers most of your questions and doesn't contain any marketing blurb. The social media feeds and forums are a great source of info as well. On top of all that it's even easy to install GrapheneOS.
Main cons: it's only available on Google Pixel phones, so if you truly despise Google and don't want to buy or use anything from them, it's not the right device/OS for you (or maybe buy it used?). However, the reason GrapheneOS is on Pixel is purely a technical one: Pixels do offer very high hardware based security already (probably the most, although iPhones have good hardware-based security as well. As is known, Apple tends to be produce good quality hardware, not quite so good software) as well as a very high degree of "platform neutrality", i.e. it's supported by Google to flash a different OS on it or use more advanced tools like adb without any sort of tinkering or unnecessary danger involved. Also you don't have to register to unlock your phone or anything, you only need to be online once to enable the OEM unlocking feature (I think this is because Google needs your IMEI to check whether the phone is carrier-locked (cannot ever be OEM unlocked) or can be unlocked, and they will immediately receive some device data including the IMEI as soon as you go online with the preinstalled Android OS once [of course they will receive some more device data than just the IMEI]), so it's best to not insert your SIM yet (and not do anything with the preinstalled OS) before you've installed GrapheneOS on your new Pixel. Do the OEM unlocking step on WiFi only, best on a public WiFi so Google has much less of a chance to identify you based on your IP or related data. Then install Graphene, then insert your SIM and start using your new phone. Other cons exist but they're rare or pretty much irrelevant in daily use. If you have to hear them, read an older post by me about some potential downsides: https://discuss.tchncs.de/post/19867254/12069767
If they can send me over the second half of my thesis I would appreciate it enormously! 😀
The analytics tools that I am personally uncomfortable with involve dynamic, changing forms of data. I run GPSLogger on my phone (without a SIM card) and continuously log the GPS data to a text file. This data is then synced to my computer when WiFi is available. I can display this data on a map using gpx-viewer, and show very detailed tracking data of myself.
I have explored this map with some friends/family. They get to see a time-stamped movie of my life - my trips to work, to the shop, when I go out, if I go on a trip, etc. The data displayed in this manner is somewhat intimate, personal information. Anyone I have shown this to has said that they would not be so comfortable with such a map of their lives existing... Well, if they are carrying a active phone with a SIM card, it does.
To think that a company like Google can own such a map for a very large number of people makes me uncomfortable. On top of that, each of those map trajectories can be associated with an individual and their personality... They have the ability to pick out specific trajectories on the basis of the political ideologies or shopping behaviors of the personas behind them. This is extreme. I am of the opinion that the convenience afforded by a these technologies does not justify the allocation of that super-power to the companies that enable the technology.
A few years ago Facebook enabled a "Graph search" feature. This allowed users to create search queries such as"Friends of friends of X who like the page "X" and went to school near Z". That tool seemed super cool on the surface, but it quickly became obvious how something like that could be easily exploited. Later on in Snowden's book I learned about XKeyscore from the NSA, which is like an extra-powerful no-consent-needed graph search that is available to some people. This is not just targeted ads.
I guess that what I am trying to convey is... For me, making the privacy-conscious choice is about not contributing to the ecosystem of very concrete tools that give super-powers to groups of people that may not have my best interest in mind. In my mind it is something very tangible and concrete, and I find many of those convenience tradeoffs to be clearly worth it.
Thanks for the sharing @[email protected]
I've check VeilidChat for the moment indeed it is just a network framework... so no apps ready yet (unless I'm mistaken )
The negative point is that the developer use exclusively google tech for it !! ( Dart, flutter )
So why peoples that want to fight for freedom use the Sauron tool !? it baffle me...
Ive used it for around a year and a half and never had any issues. My banking app stopped working after about 8 months but I just log in via a browser and it hasn't effected my life at all.
For anyone considering the move here is a list of bank apps and their current working status as I know that is a big consideration people worry over.
I wish I could be more help, but its always worked for me since I started using GrapheneOS about 4 years ago.
The one thing I can think of is a misconfiguration on SUPL and PSDS.
If you still have access to a GrapheneOS device maybe you could take a look there.


For anyone who seems uninterested, ask if they'd like to be arrested for murder simply because they biked past a place every day.
For anyone looking for great talking points about this issue, I highly recommend "Taking Control of Your Personal Data" by prof. Jennifer Golbeck, published by The Teaching Company, ISBN:978-1629978390, likely available at your local library as a DVD or streaming.
