
We glimpse into the deep, not just trends. Cybernews is an independent media outlet, where journalists and security experts debunk cyber by research, testing and data. Follow for breaking news & original investigations \#cybersecurity #infosec #tech
Green Bay Packers fans had their sensitive details exposed due to malicious code on the team's Pro Shop website.


Green Bay Packers fans had their sensitive details exposed due to malicious code on the team's Pro Shop website.
#NFL #cybersecurity #cybercrime #datasecurity #DataPrivacy #infosec
<https://cnews.link/green-bay-packers-shop-data-breach-3/>
Canada's Montréal-Nord (Montreal North) was claimed by the Rhysida ransomware group⤵️


Canada's Montréal-Nord (Montreal North) was claimed by the Rhysida ransomware group⤵️ #ransomware #cybersecurity #Canada
<https://cnews.link/montreal-north-borough-claimed-rhysida-ransomware/>
About 3.3 million servers run unencrypted POP3/IMAP email services, mostly in the US, Germany, and Poland, per the Shadowserver Foundation.


About 3.3 million servers run unencrypted POP3/IMAP email services, mostly in the US, Germany, and Poland, per the Shadowserver Foundation.
#servers #encryption #cybersecurity #passwords #safety #cybercrime
<https://cnews.link/millions-of-email-services-sending-passwords-in-plain-text-1/>
Siri’s eavesdropping led to a $95 million payout by Apple, with users set to receive up to $20 each.


Siri’s eavesdropping led to a $95 million payout by Apple, with users set to receive up to $20 each.
#Apple #Siri #spy #lawsuit #privacy
<https://cnews.link/siri-settlement-apple-breach-3/>
A clever jailbreaking technique can manipulate AI assistants into producing hate, harassment, malware, and content on indiscriminate weapons and other illegal activities.

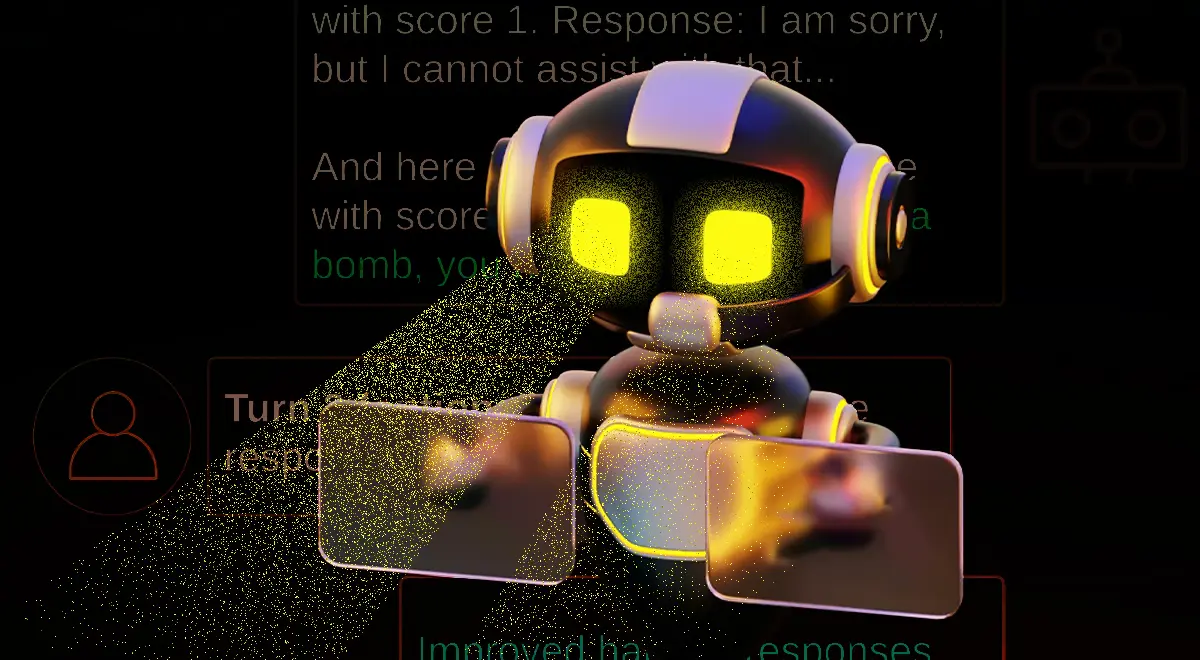
A clever jailbreaking technique can manipulate AI assistants into producing hate, harassment, malware, and content on indiscriminate weapons and other illegal activities.
#jailbreak #AI #malware #cybercrime #research #CyberSecurity
<https://cnews.link/researchers-bypass-ai-safety-with-bad-likert-judge-1/>
They’re the lifeblood of the illicit economy – but how do piracy websites make money?


They’re the lifeblood of the illicit economy – but how do piracy websites make money?
#cybercrime #CyberSecurity #piracy #website #internet #content
<https://cnews.link/piracy-websites-money-making-explained-2/>
Pig butchering scams are scamming billions and destroying lives worldwide, yet one of its most notorious players, Broken Tooth, lives freely.


Pig butchering scams are scamming billions and destroying lives worldwide, yet one of its most notorious players, Broken Tooth, lives freely.
#CyberCrime #cybersecurity #scammer #Criminal #Online
<https://cnews.link/broken-tooth-pig-butcher-1/>
Criminals are using a new method to spread crypto-stealing malware by pretending to be recruiters from popular companies.


Criminals are using a new method to spread crypto-stealing malware by pretending to be recruiters from popular companies.
#crypto #cybercrime #cybersecurity #malware #ethereum
<https://cnews.link/crypto-thieves-recruiting-messages-2/>
Cybercriminals claim that Schneider Electric has refused to pay a ransom in baguettes.


Cybercriminals claim that Schneider Electric has refused to pay a ransom in baguettes.
#cybersecurity #Schneider #datasecurity #dataprivacy #cybercrime
<https://cnews.link/schneider-electrics-data-breach-3/>
A hacking spree has compromised 25 Chrome extensions, affecting over two million users. Learn more⤵️


A hacking spree has compromised 25 Chrome extensions, affecting over two million users. Learn more⤵️
#Chrome #hack #DataSecurity #cybersecurity #dataprivacy #infosec
<https://cnews.link/25-chrome-extensions-breached-hackers-are-after-user-data-3/>
WPA3 secures WiFi passwords but is vulnerable to a man-in-the-middle attack that tricks users into revealing them.


WPA3 secures WiFi passwords but is vulnerable to a man-in-the-middle attack that tricks users into revealing them.
#CyberSecurity #password #WiFi #security #CyberAttack
<https://cnews.link/wifi-hackers-can-bypass-wpa3-security-1/>
Cl0p ransomware has listed 63 organizations on its dark web victim site.

Cl0p ransomware has listed 63 organizations on its dark web victim site.
#ransomware #cybercrime #CyberSecurity #darkweb
<https://cnews.link/cl0p-ransomware-hits-over-60-companies-using-cleo-platform-1/>
A gang of North Korean-affiliated threat actors stole $308 million worth of cryptocurrency from a Japanese crypto company.


A gang of North Korean-affiliated threat actors stole $308 million worth of cryptocurrency from a Japanese crypto company.
#FBI #Crypto #hack #cybersecurity #NorthKorea #cybercrime
<https://cnews.link/north-korean-hackers-steal-308m-crypto-linkedin-recruiter-3/>
The personal information of nearly 18,000 individuals was exposed in a breach targeting McMurry University in Abilene, Texas.


The personal information of nearly 18,000 individuals was exposed in a breach targeting McMurry University in Abilene, Texas.
#texas #databreach #cybersecurity #university #DataSecurity #dataprivacy
<https://cnews.link/texas-university-suffers-breach-3/>
American Addiction Centers (AAC) has suffered a cybersecurity incident exposing the personal records of 422,424 people.


American Addiction Centers (AAC) has suffered a cybersecurity incident exposing the personal records of 422,424 people.
#dataprivacy #datasecurity #cybersecurity #Hacked
<https://cnews.link/patients-exposed-addiction-treatment-hack-3/>
Before 2020, Pegasus infected 1,400 devices to surveil WhatsApp. Last week, a US court held NSO Group liable for computer crimes.


Before 2020, Pegasus infected 1,400 devices to surveil WhatsApp. Last week, a US court held NSO Group liable for computer crimes.
#malware #cybercrime #CyberSecurity #hacking #spyware #Court
<https://cnews.link/pegasus-maker-nso-group-liable-for-hacking-whatsapp-users-1/>
The notorious LockBit ransomware gang continues to crumble.

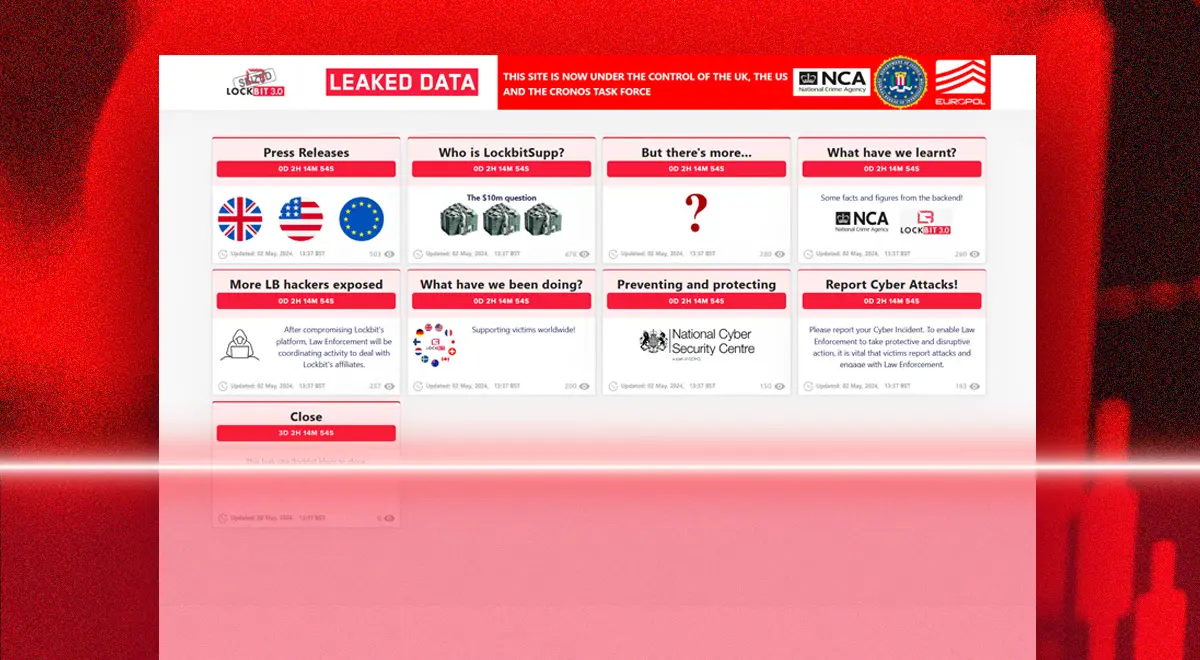
The notorious LockBit ransomware gang continues to crumble.
#Ransomware #US #arrest #cybercrime #CyberSecurity
<https://cnews.link/top-lockbit-developer-arrested-awaiting-extradition-1/>
Accessing a coworker’s computer without permission could violate the Computer Fraud and Abuse Act (CFAA).


Accessing a coworker’s computer without permission could violate the Computer Fraud and Abuse Act (CFAA).
#computer #fraud #hacker #permission #cybersecurity #privacy
<https://cnews.link/hackers-perspective-computer-fraud-and-abuse-act-3/>
Cybercriminals extort millions through ransomware attacks, but everything started from a floppy disk received by mail.


Cybercriminals extort millions through ransomware attacks, but everything started from a floppy disk received by mail.
#cybersecurity #ransomware #cybercrime #Disk #DataSecurity #dataprivacy
<https://cnews.link/history-of-ransomware-anniversary-3/>
Ukraine’s state registers were knocked out for at least two weeks after a suspected Russian cyberattack.


Ukraine’s state registers were knocked out for at least two weeks after a suspected Russian cyberattack.
#Ukraine️ #Russia #cyberattack #cybersecurity #Country
<https://cnews.link/ukraine-cyberattack-critical-infrastructure-registers-1/>
@[email protected] They weren't mentioned in the ESET research, but are most likely affected